TINAELLIS\Cybersecurity
Welcome to my blog!
Windows Registry Forensics
The FTK forensics toolkit provides us with built-in reports that allow us to dig into the data stored in Windows Registry, without the OS interfering with our investigation.
View Registry Files with FTK Forensics Toolkit
Generate FTK Forensics Report
- Open FTK
- Select “Go directly to working in program” to skip startup
- File > Add Evidence
- Select Image
- Processes to Perform > Check “Registry Reports” > Uncheck everything else (unless items are needed in report)
- Select Next
- Add Evidence
- Select Next
- Finish
- Navigate to Tools > Select Registry Reports
- Select “Check All” and Ok
- Navigate to File > Report Wizard
- Leave defaults on each page (unless you need something specific)
- Report Location > Make sure “Include Registry Viewer reports” is checked
- Finish
- Select “Yes” to view the report
Navigating FTK Report
From Case Summary > Registry Report
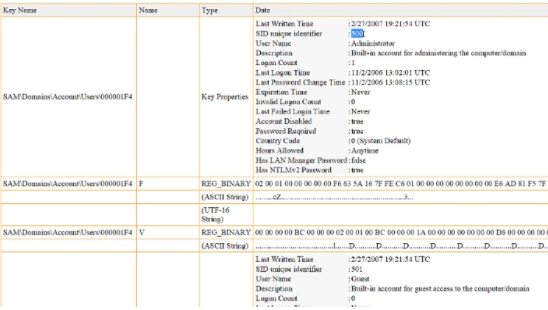
SAM - Users Report
This report includes a list of users and their SID’s. SIDs of 500 are typically for administrators, 501 is for guests. SIDs that start in the 1000s are usually where the user IDs are.
Summary Report Software - OS Version
This report provides us with information on the OS (or software selected). It includes information such as what company licensed the software, when it was installed, and current version.
Summary Report: System - Time Zone Settings
This should help you understand the time zone that the image was created in. It provides information based upon the time zone that is stored in UTC time.
FTK Demo Limitations
One limitation of the FTK demo program is that it only allows us to examine 5000 files. To limit the number of files that we are examining in FTK, we can pull out the items in Windows Registry that we want to focus on. This can be done using FTK Imager.
If file size limitation occurs in FTK - use this process to isolate registry files:
FTK Imager
Exporting Registry Files with FTK Imager
- Open AccessData FTK Imager
- File > Add Evidence Item
- Select Image
- Navigate to the folders and files you want to export in the evidence tree.
- Four S files are found in the config folder: Image > Partition > NONAME [NTFS] > Root > WINDOWS > system32 > config
- Hold down ctrl key to select multiple items + Right Click
- Export Files > Save
When you grab the Four S folders and files, you also need to grab NTuser.dats.
- This can be found at Image > Partition > NONAME [NTFS] > Root > users >
AccessData Registry Viewer
View Registry Files with AccessData Registry Viewer
AccessData Registry Viewer is a tool that we can use to navigate into files that Registry Editor protects us from viewing. It works as a replacement for RegEdit.
- Use FTK Imager first to export registry files from an image.
- Open Registry Viewer > No (to run in demo mode)
- Click Open (folder icon) > Browse and select Hive you want to open
- Double Click to open
- Expand tree (example) SAM > Domains > Account > Users