TINAELLIS\Cybersecurity
Welcome to my blog!
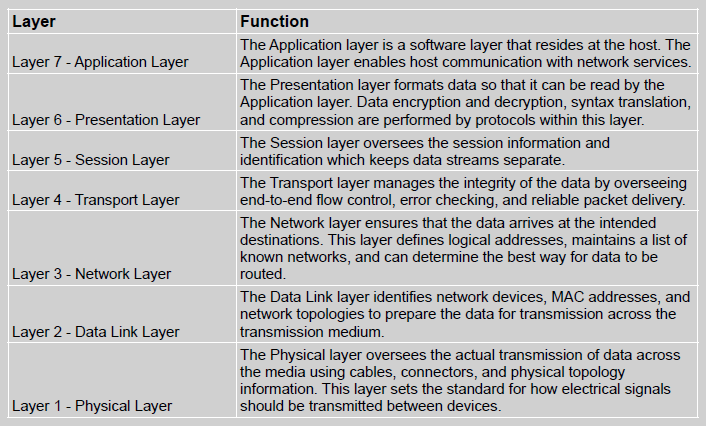
OSI Model
Functions and Protocols at a Glance
Application (L7)
PDU: Data
Layer 7: works closest to the user and provides file transmissions, message exchanges, terminal sessions, and much more. This layer does not include the actual applications, but rather the protocols that support the applications.
- Defines the interface to user processes
- Provides standardized network services
L7 PROTOCOLS
Protocol Function: The protocols at the application layer handle file transfer, virtual terminals, network management, and fulfilling networking requests of applications.
- File Transfer Protocol (FTP)
- Network Time Protocol (NTP)
- Simple Mail Transfer Protocol (SMTP)
- Internet Message Access Protocol (IMAP)
- Hypertext Transfer Protocol (HTTP)
- Dynamic Host Configuration Protocol (DHCP)
- UDP-based Protocol
- DHCP manipulates L2 based on responses arriving through L7
- Domain Name System (DNS) - DNS is an application layer protocol, because DNS query and answer is the application level communications.
Presentation (L6)
PDU: Data
Layer 6: receives information from the application layer protocol and puts it in a format that any process operating at the same layer on a destination computer following the OSI model can understand. This layer provides a common means of representing data in a structure that can be properly processed by the end system. The presentation layer is concerned not with the meaning of data but with the syntax and format of that data.
- Specifies architecture-independent data transfer format
- Encodes and decodes data; Encrypts and decrypts data; Compresses and decompresses data
Presentation Layer works as a Translator
It translates the format an application is using to a standard format that can be sent over the network. It adds information to tell the destination computer the file type and how to process and present it.
L6 PROTOCOLS (no protocols, just services)
The services of the presentation layer handle translation into standard formats, data compression and decompression, and data encryption and decryption. No protocols work at this layer, just services. The following lists some of the presentation layer standards:
- American Standard Code for Information Interchange (ASCII)
- Tagged Image File Format (TIFF)
- Joint Photographic Experts Group (JPEG)
- Motion Picture Experts Group (MPEG)
- Musical Instrument Digital Interface (MIDI)
Session (L5)
PDU: Data
Layer 5: is responsible for establishing a connection between the two applications, maintaining it during the transfer of data, and controlling the release of this connection. When the conversation is over, this path is broken down and all parameters are set back to their original settings. This process is known as dialog management (dialog control).
- Manages user sessions and dialogues
- Controls establishment and termination of logical links between users
L5 PROTOCOLS
The session layer protocols set up connections between applications; maintain dialog control; and negotiate, establish, maintain, and tear down the communication channel. Some of the protocols that work at this layer include:
- Layer 2 Tunneling Protocol (L2TP)
- Network Basic Input Output System (NetBIOS)
- Password Authentication Protocol (PAP)
- Point-to-Point Tunneling Protocol (PPTP)
- Remote Procedure Call (RPC)
L5 PROTOCOL SECURITY
Session layer protocols are the least used protocols in a network environment; Many of them should be disabled on systems to decrease the chance of them being exploited. RPC, NetBIOS, and similar distributed computing calls usually only need to take place within a network; thus, firewalls should be configured so this type of traffic is not allowed into or out of a network. Firewall filtering rules should be in place to stop this type of unnecessary and dangerous traffic.
L5 MODES
The session layer protocol can enable communication between two applications to happen in three different modes:
- Simplex Communication - takes place in one direction, though in practice this is very seldom the case.
- Half-duplex Communication - takes place in both directions, but only one application can send information at a time.
- Full-duplex Communication - takes place in both directions, and both applications can send information at the same time.
L5 VERSUS L4
The functionality of the session and transport layers is similar insofar as they both set up some type of session or virtual connection for communication to take place. The difference is that protocols that work at the session layer set up connections between applications, whereas protocols that work at the transport layer set up connections between computer systems.
- Session layer protocols control application-to-application communication.
- Transport layer protocols handle computer-to-computer communication.
Transport (L4)
PDU: Segment
Layer 4: When two computers are going to communicate through a connection-oriented protocol, they first agree on how much information each computer will send at a time, how to verify the integrity of the data once received, and how to determine whether a packet was lost along the way. The two computers agree on these parameters through a handshaking process at the transport layer.
- Provides reliable and sequential end-to-end packet delivery
- Provides connectionless oriented packet delivery
L4 PROTOCOLS
The protocols at the transport layer handle end-to-end transmission and segmentation of a data stream. The following protocols work at this layer:
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
- Stream Control Transmission Protocol (SCTP)
- Resource Reservation Protocol (RSVP)
- QUIC (not an acronym)
Network (L3)
PDU: Packet
Layer 3: The main responsibilities of layer 3, are to insert information into the packet’s header so it can be properly addressed and routed, and then to actually route the packet to its proper destination. In a network, many routes can lead to one destination. The protocols at the network layer must determine the best path for the packet to take. Routing protocols build and maintain their routing tables.
- Routes packets according to unique network addresses
L3 PROTOCOLS
The responsibilities of the network layer protocols include internetworking service,addressing, and routing. The following lists some of the protocols that work at this layer:
- Internet Protocol (IP)
- Internet Control Message Protocol (ICMP), (ping utility)
- Internet Group Management Protocol (IGMP)
- Routing Information Protocol (RIP)
- Open Shortest Path First (OSPF)
Data Link (L2)
PDU: Frame
Layer 2: Different networking technologies can use different protocols, network interface cards (NICs), cables, and transmission methods. Each of these components has a different header data format structure, and they interpret electromagnetic signals in different ways. The data link layer is where the network stack knows in what format the data frame must be in order to transmit it properly over Ethernet, wireless, or frame relay links.
- Defines procedures for operating the communication link
- Provides framing and sequencing
L2 PROTOCOLS
The protocols at the data link layer convert data into LAN or WAN frames for transmission and define how a computer accesses a network. This layer is divided into the Logical Link Control (LLC) and the Media Access Control (MAC) sublayers. Some protocols that work at this layer include the following:
- Address Resolution Protocol (ARP)
- Reverse Address Resolution Protocol (RARP)
- Serial Line Internet Protocol (SLIP)
- Ethernet (IEEE 802.3)
- Wireless Ethernet (IEEE 802.11)
The data link layer can be further divided into two functional sublayers:
- Logical Link Control (LLC), whose job is to interface with the network layer above, and
- Media Access Control (MAC), which is designed to interface with the physical layer below
Logical Link Control (LLC) Sublayer
The LLC sublayer takes care of flow control and error checking. Data coming from the network layer passes down through the LLC sublayer and goes to the MAC sublayer.
Generally, LLC is implemented in software (as a device driver)
Media Access Control (MAC) Sublayer
The technology at the MAC sublayer knows if the network is Ethernet, wireless, or frame relay, so it knows how to put the last header and trailer on the packet before it “hits the wire” for transmission.
MAC is built-in firmware on a physical device
Network Interface Card (NIC)
NICs bridge the data link and physical layers. Data is passed down through the first six layers and reaches the NIC at the data link layer. Depending on the network technology being used, the NIC encodes the bits at the data link layer, which are then turned into electricity states at the physical layer and placed onto the wire for transmission.
Layer 2 Security Standards, include defending against: Packet sniffing, modifying headers, and spoof traffic.
Physical (L1)
PDU: Bits
Layer 1: converts bits into electromagnetic signals for transmission.
- Defines the physical means of sending data over network devices.
L1 PROTOCOLS
Network interface cards and drivers convert bits into electrical signals and control the physical aspects of data transmission, including optical, electrical, and mechanical requirements. The following are some of the standard interfaces at this layer:
- RS/EIA/TIA-422, RS/EIA/TIA-423, RS/EIA/TIA-449, RS/EIA/TIA-485
- 10Base-T, 10Base2, 10Base5, 100Base-TX, 100Base-FX, 100Base-T, 1000Base-T, 1000Base-SX
- Integrated Services Digital Network (ISDN)
- Digital subscriber line (DSL)
- Synchronous Optical Networking (SONET)
CONVERTING BITS INTO ELECTRONIC SIGNALS
Signals and voltage schemes have different meanings for different LAN and WAN technologies. If a user sends data through the radio transceiver on a smartphone, the data format, electrical signals, and control functionality are much different than if that user sends data through an Ethernet NIC and onto an unshielded twisted pair (UTP) wire for LAN communication. The mechanisms that control this data going onto the radio waves, or the UTP wire, work at the physical layer.
- This layer controls synchronization, data rates, line noise, and transmission techniques.
- Specifications for the physical layer include the timing of voltage changes, voltage levels, and the physical connectors for electrical, optical, and mechanical transmission.